The Ultimate Guide To Risk Management Enterprise
Table of ContentsThe Definitive Guide for Risk Management EnterpriseRisk Management Enterprise Fundamentals ExplainedA Biased View of Risk Management Enterprise
Control who can watch or modify these components by establishing certain accessibility civil liberties for private customers, ensuring details safety and customized use. Enables users to tailor their interface by picking and preparing important data components. Supplies an individualized experience by enabling personalization of where and just how data elements are presented.It enables accessibility to real-time integrated data immediately. Centers can make use of comprehensive data knowledge for quicker and more educated decision-making.
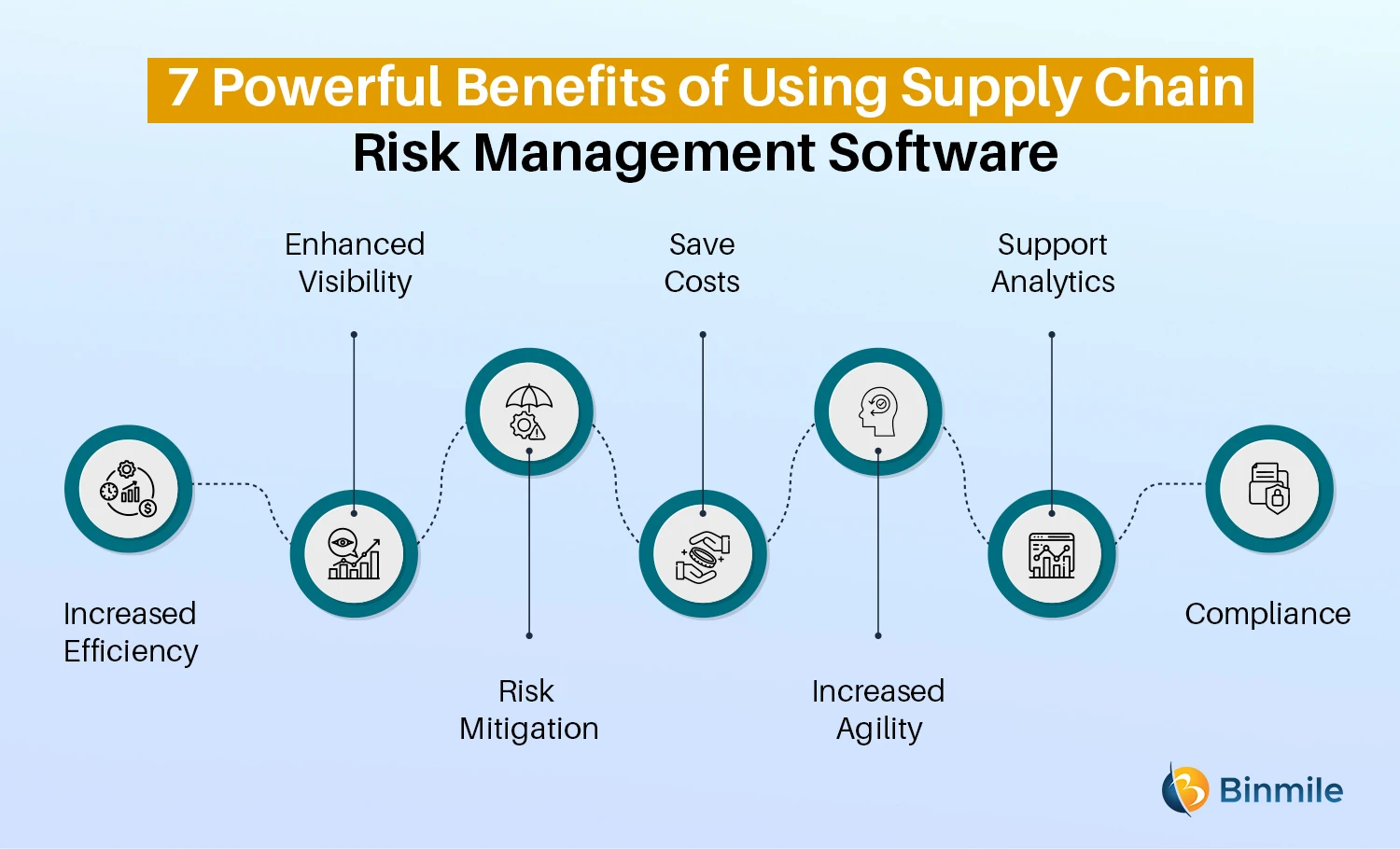
Diligent is a danger monitoring software that permits enhancing efficiency, and enhances development. It also aids monitor dangers with ERM software application that includes integrated analytics and adapts to your service demands.
More About Risk Management Enterprise
Streamlines the procedure of gathering risk information from different components of the company. Gives leadership and the board with real-time risk understandings. Usage ACL's sophisticated analytics to identify risk patterns and predict dangers.
This allows companies to catch risk understandings and red flags in the third-party supplier's protection report. Allows business to record and document risk insights and red flags in third-party supplier safety and security reports.
It likewise minimizes risk through streamlined compliance and threat monitoring. It can help gather and track all your risks in the Hyperproof danger register.
It makes certain that everything is organized and accessible for auditors. Utilizes automation to maintain evidence updated while reducing manual effort. It supplies fast access to necessary information and paperwork. This ensures the safety of Active proof instances by making it possible for multi-factor verification (MFA) utilizing authenticator applications such as Google Authenticator, Microsoft Authenticator, or Authy.
Getting My Risk Management Enterprise To Work
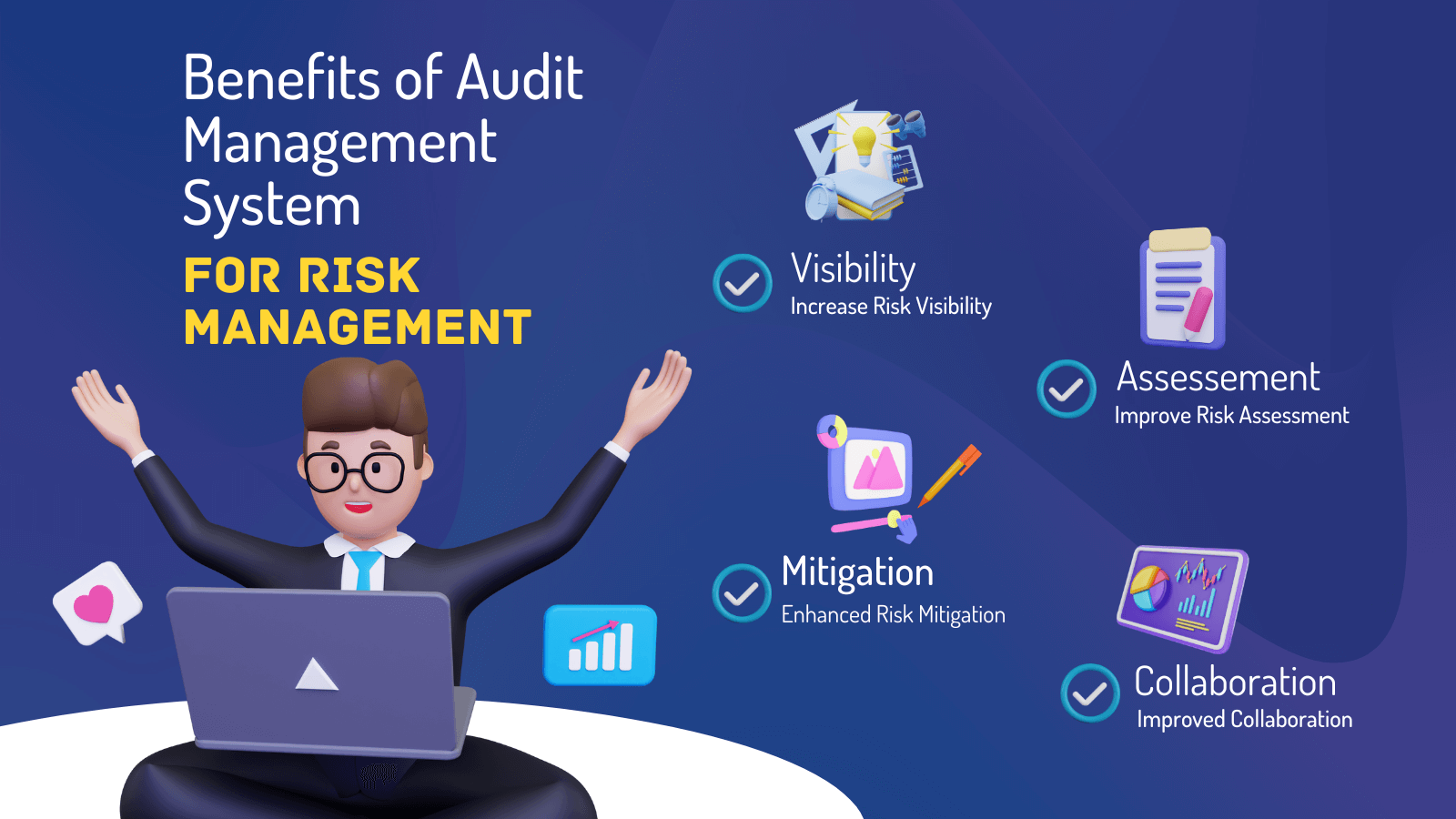
It enables smooth workflows and integrations and decreases ineffectiveness. It gives top-tier safety and security features to guard delicate data. This danger monitoring software program is an excellent device for centers wanting to deal with unnecessary problems or risks. It features several kinds of attributes that make it specific for ERM managers. Here we have highlighted a few of its vital attributes for your advantage, so have a helpful site look.
Users can likewise use the AI-powered devices and pre-existing material to develop, examine, prioritize, and address dangers successfully. Streamlines the you could try here procedure of setting up and occupying threat signs up.